Current Issue
lssue 6, 2025
Editors-in-Chief
Yunhe Pan, Aiguo Fei
Advisor Xicheng Lu
ISSN 2095-9184
CN 33-1389/TP
IF (2024 JCR) 2.9
| Submit Now |
- Current Issue
- Cover Articles
- Archive
- Virtual Issues
- Online First
Regular Papers
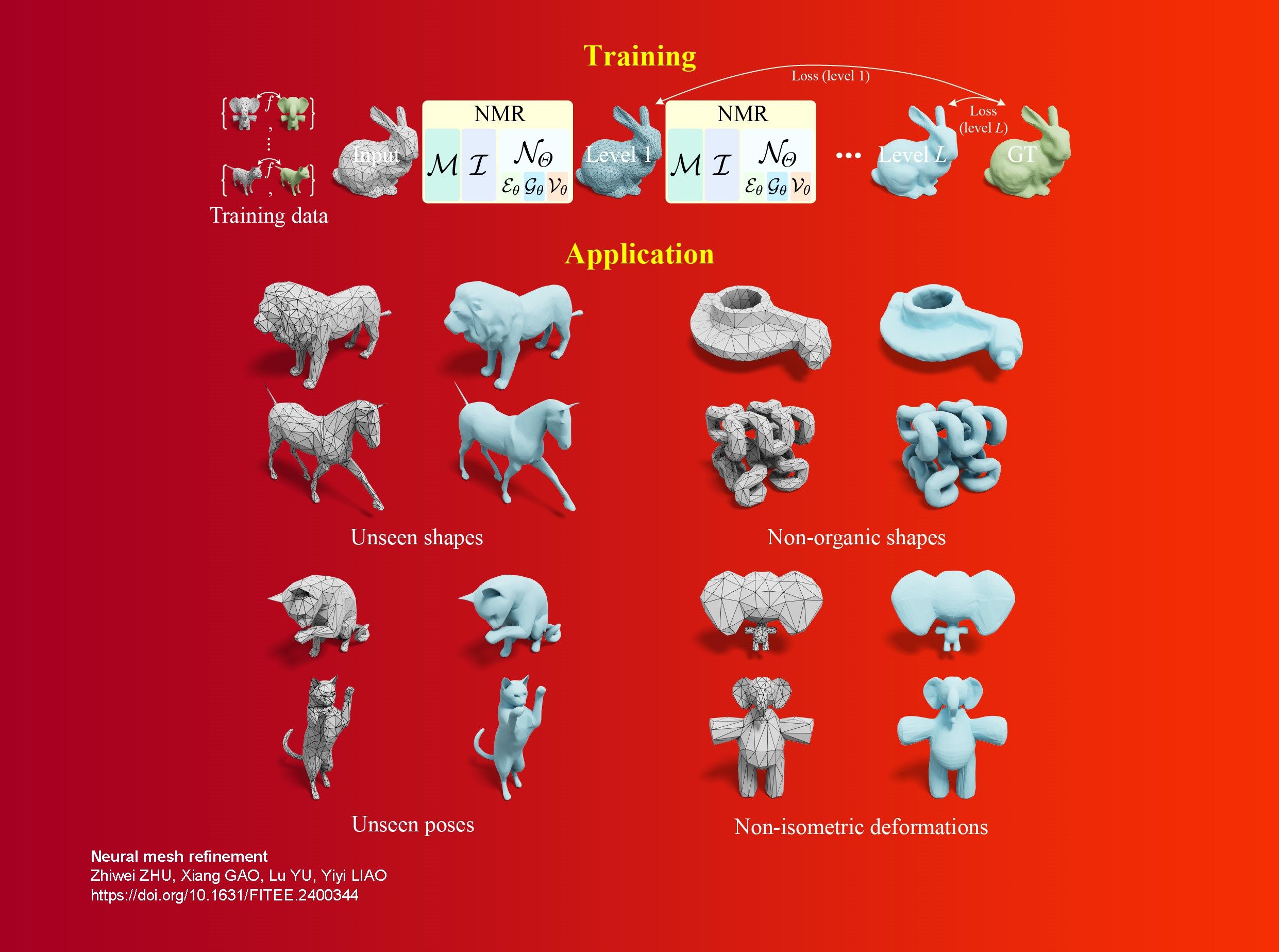
MAL: multilevel active learning with BERT for Chinese textual affective structure analysis Enhanced Publication
Abstract:Chinese textual affective structure analysis (CTASA) is a sequence labeling task that often relies on supervised deep learning methods. However, acquiring a large annotated dataset for training can be costly and time-consuming. Active learning offers a solution by selecting the most valuable samples to reduce labeling costs. Previous approaches focused on uncertainty or diversity but faced challenges such as biased models or selecting insignificant samples. To address these issues, multilevel active learning (MAL) is introduced, which leverages deep textual information at both the sentence and word levels, taking into account the complex structure of the Chinese language. By integrating the sentence-level features extracted from bidirectional encoder representations from Transformers (BERT) embeddings and the word-level probability distributions obtained through a conditional random field (CRF) model, MAL comprehensively captures the Chinese textual affective structure (CTAS). Experimental results demonstrate that MAL significantly reduces annotation costs by approximately 70% and achieves more consistent performance compared to baseline methods.Keywords:Sentiment analysis;Sequence labeling;Active learning (AL);Bidirectional encoder representations from Transformers (BERT)36|18|0Updated:2025-07-02Regular Papers
SPJEU: a self-sufficient plaintext-related JPEG image encryption scheme based on a unified key Enhanced Publication AI Introduction
“In the field of image encryption, a self-sufficient plaintext-related JPEG image encryption scheme based on a unified key (SPJEU) has been proposed. This scheme establishes the connection between the plaintext and the key by selecting the direct current (DC) coefficients in the JPEG image through a unified key, and applies homomorphic encryption to the selected DC coefficients. Extensive experiments show that our scheme can resist chosen plaintext attacks, avoid transmitting plaintext-related additional data in the communication channel, and simplify key management.”Abstract:In recent research on image encryption, many schemes associate the key generation mechanism with the plaintext to resist chosen plaintext attacks. However, when the sender encrypts many images, a large amount of additional data related to the plaintext need to be transmitted, which leads to problems such as high transmission costs, high requirements for key storage space, and complex key management. Therefore, in this paper, we propose a self-sufficient plaintext-related JPEG image encryption scheme based on a unified key (SPJEU). This scheme establishes the connection between the plaintext and the key by selecting the direct current (DC) coefficients in the JPEG image through a unified key. Homomorphic encryption is applied to the selected DC coefficients, allowing plaintext information to be decrypted directly from the ciphertext domain using a specific calculation method. The remaining DC coefficients are encrypted through group diffusion, and the alternating current (AC) coefficients are grouped and permuted based on the run length. Extensive experiments show that our scheme can resist chosen plaintext attacks, avoid transmitting plaintext-related additional data in the communication channel, and simplify key management. This scheme also ensures the security and format compatibility of the ciphertext image, and the file increment after encryption is very small.Keywords:Image encryption;Self-sufficient;Plaintext-related;JPEG;Homomorphic encryption10|12|0Updated:2025-07-02Regular Papers
A subspace-based few-shot intrusion detection system for the Internet of Things
◇ Enhanced Publication AI Introduction“In the field of IoT security, researchers have made progress in few-shot intrusion detection. They proposed a subspace-based approach for few-shot IoT intrusion detection systems, which constructs a subspace for each category and calculates the distance between query samples and the subspace to detect malicious samples. This provides a solution to address the dilemma of insufficient learnable samples in real-world IoT environments.”Abstract:Deep learning-based intrusion detection systems rely on numerous training samples to achieve satisfactory detection rates. However, in the real-world Internet of Things (IoT) environments, the diversity of IoT devices and the subsequent fragmentation of attack types result in a limited number of training samples, which urgently requires researchers to develop few-shot intrusion detection systems. In this study, we propose a subspace-based approach for few-shot IoT intrusion detection systems to cope with the dilemma of insufficient learnable samples. The method is based on the principle of classifying metrics to identify network traffic. After feature extraction of samples, a subspace is constructed for each category. Next, the distance between the query samples and the subspace is calculated by the metric module, thus detecting malicious samples. Subsequently, based on the CICIoT2023 dataset we construct a few-shot IoT intrusion detection dataset and evaluate the proposed method. For the detection of unknown categories, the detection accuracy is 93.52% in the 5-way 1-shot setting, 92.99% in the 5-way 5-shot setting, and 93.65% in the 5-way 10-shot setting.Keywords:Intrusion detection system;Few-shot learning;Internet of Things;Subspace15|5|0Updated:2025-07-02Regular Papers
CUSMART: effective parallelization of string matching algorithms using GPGPU accelerators Enhanced Publication AI Introduction
“In the field of string matching algorithms, researchers have introduced their research progress. Expert developed the CUDA-enhanced SMART (CUSMART) library, which incorporates parallelized iterations of 64 string matching algorithms, leveraging the CUDA application programming interface. This provides solutions to solve string matching problems and lays a foundation for the construction of high-performance string matching systems.”Abstract:This study presents a parallel version of the string matching algorithms research tool (SMART) library, implemented on NVIDIA’s compute unified device architecture (CUDA) platform, and uses general-purpose computing on graphics processing unit (GPGPU) programming concepts to enhance performance and gain insight into the parallel versions of these algorithms. We have developed the CUDA-enhanced SMART (CUSMART) library, which incorporates parallelized iterations of 64 string matching algorithms, leveraging the CUDA application programming interface. The performance of these algorithms has been assessed across various scenarios to ensure a comprehensive and impartial comparison, allowing for the identification of their strengths and weaknesses in specific application contexts. We have explored and established optimization techniques to gauge their influence on the performance of these algorithms. The results of this study highlight the potential of GPGPU computing in string matching applications through the scalability of algorithms, suggesting significant performance improvements. Furthermore, we have identified the best and worst performing algorithms in various scenarios.Keywords:String matching;Parallel programming;Graphics processing unit (GPU) programming;General-purpose computing on GPU (GPGPU);NVIDIA;Compute unified device architecture (CUDA);String matching algorithms research tool (SMART)15|17|0Updated:2025-07-02Regular Papers
Federated model with contrastive learning and adaptive control variates for human activity recognition Enhanced Publication AI Introduction
“In the field of human activity recognition, researchers have introduced FedCoad, a novel federated learning model that leverages contrastive learning with adaptive control variates to address data skewness among clients, enhancing model convergence and outperforming state-of-the-art FL algorithms on HAR benchmark datasets.”Abstract:Recent attention to privacy issues demands a communication-safe method for training human activity recognition (HAR) models on client activity data. Federated learning (FL) has become a compelling technique to facilitate model training between the server and clients while preserving data privacy. However, classical FL methods often assume independent and identically distributed (IID) data among clients. This assumption does not hold true in practical scenarios. Human activity in real-world scenarios varies, resulting in skewness where identical activities are executed uniquely across clients. This leads to local model objectives drifting away from the global model objective, thereby impeding overall convergence. To address this challenge, we propose FedCoad, a novel federated model leveraging contrastive learning with adaptive control variates to handle the skewness among HAR clients. Model contrastive learning minimizes the gap in representation between global and local models to help global model convergence. During local model updates, the adaptive control variates penalize the local model updates with respect to the model weight and the rate of change from the control variates update. Our experiments show that FedCoad outperforms state-of-the-art FL algorithms on HAR benchmark datasets.Keywords:Federated learning (FL);Human activity recognition (HAR);Contrastive learning;Deep learning14|11|0Updated:2025-07-02Regular Papers
Prototype-guided cross-task knowledge distillation Enhanced Publication AI Introduction
“In the field of knowledge distillation, researchers have proposed a prototype-guided cross-task knowledge distillation (ProC-KD) method. This approach transfers the teacher network's local-level object knowledge to various task scenarios, enhancing the student network's generalization ability. It provides a solution to address the challenge of different label spaces in cross-task knowledge distillation.”Abstract:Recently, large-scale pretrained models have revealed their benefits in various tasks. However, due to the enormous computation complexity and storage demands, it is challenging to apply large-scale models to real scenarios. Existing knowledge distillation methods require mainly the teacher model and the student model to share the same label space, which restricts their application in real scenarios. To alleviate the constraint of different label spaces, we propose a prototype-guided cross-task knowledge distillation (ProC-KD) method to migrate the intrinsic local-level object knowledge of the teacher network to various task scenarios. First, to better learn the generalized knowledge in cross-task scenarios, we present a prototype learning module to learn the invariant intrinsic local representation of objects from the teacher network. Second, for diverse downstream tasks, a task-adaptive feature augmentation module is proposed to enhance the student network features with the learned generalization prototype representations and guide the learning of the student network to improve its generalization ability. Experimental results on various visual tasks demonstrate the effectiveness of our approach for cross-task knowledge distillation scenarios.Keywords:Knowledge distillation;Cross-task;Prototype learning14|19|0Updated:2025-07-02
0 1 Hybrid-augmented intelligence: collaboration and cognition
0 3 Applications of artificial intelligence in intelligent manufacturing: a review*
0 5 Challenges and opportunities: from big data to knowledge in AI 2.0
0 6 Recent advances in efficient computation of deep convolutional neural networks
0 7 Terahertz time-domain spectroscopy and micro-cavity components for probing samples: a review
0 8 Cross-media analysis and reasoning: advances and directions
0 9 Current trends in the development of intelligent unmanned autonomous systems
Videos
-
 00:02:51
00:02:512023 Issue 1 | Scalability and efficiency challenges for the exascale supercomputing system: practice of a parallel supporting environment on the Sunway exascale prototype system
2023-12-30Play Total: 23 -
 00:02:30
00:02:302023 Issue 6 | Model division multiple access for semantic communications
2023-12-30Play Total: 12 -
 00:02:15
00:02:152022 Issue 10 | Discussion on a new paradigm of endogenous security towards 6G networks
2023-12-30Play Total: 0 -
 00:02:22
00:02:222022 Issue 12 | Technology trends in large-scale high-efficiency network computing
2023-12-30Play Total: 2 -
 00:02:48
00:02:482022 Issue 6 | Self-deployed execution environment for high performance computing
2022-08-03Play Total: 7 -
 00:02:24
00:02:242022 Issue 2 | A full-process intelligent trial system for smart court
2022-05-17Play Total: 7 -
 00:02:37
00:02:372022 Issue 3 | Automatic protocol reverse engineering for industrial control systems with dynamic taint analysis
2022-05-17Play Total: 4 -
 00:05:36
00:05:36P1 Speech by Academician Baoyan Duan
2022-04-17Play Total: 9 -
 00:02:27
00:02:27P2 Speech by Professor Min Sheng, Xidian University
2022-04-17Play Total: 6 -
 00:02:37
00:02:37P3 Speech by Professor Yunsong Li, Xidian University
2022-04-17Play Total: 10